
The law vs. LockBit: A global effort against cybercrime (Source – Shutterstock)
Law enforcement strikes back with rewards: the fall of a major cybercrime syndicate, LockBit
- Operation Cronos unites global law enforcement to strike the LockBit cybercrime group, leading to significant disruptions.
- Despite crackdowns, LockBit persists, changing tactics to continue its cybercriminal activities.
- The fight against LockBit exemplifies a unified international response to combat rising ransomware threats.
Recent developments in the cybersecurity industry have seen a significant collaborative effort by law enforcement agencies, resulting in a major setback to a leading ransomware gang’s operations. Known as Operation Cronos, this joint initiative involved agencies from 11 countries, all aiming to dismantle the LockBit group.
Despite law enforcement’s success in seizing control of several websites associated with LockBit, the ransomware gang remains active on other online platforms. Reports suggest that some of the gang’s dark web sites, which host data and enable private messaging, are still operational.
In a recent Tweet, VX-Underground shared a statement from the LockBit group. The group has shifted to using Tox, a chat application, for communications, especially with those who have failed payment transactions. They assured victims that the servers holding the stolen data were secure from FBI intervention and announced plans to publish this data on a new blog after rebuilding.
US law enforcement’s reward strategy in the cybercrime battle against LockBit
Reuters recently reported that the US government has offered a substantial reward for information leading to the leaders of the LockBit cybercrime group. The reward, up to US$15 million, accompanies news from Ukrainian police about the arrest of a father-son duo allegedly involved with the gang.
The actions against LockBit represent a concerted effort by international law enforcement to combat online criminal gangs that encrypt victims’ data for extortion purposes. The US, UK, and EU have recently disrupted the group through an aggressive operation, turning the hackers’ own site against them. This operation included releasing data and a decryption tool for the gang’s victims. Additionally, the US has imposed sanctions and filed indictments against two of the group’s key operatives.
The State Department issued a statement, opening a new tab, detailing the reward of up to US$15 million for information that leads to the arrest and conviction of the ransomware group’s leaders.
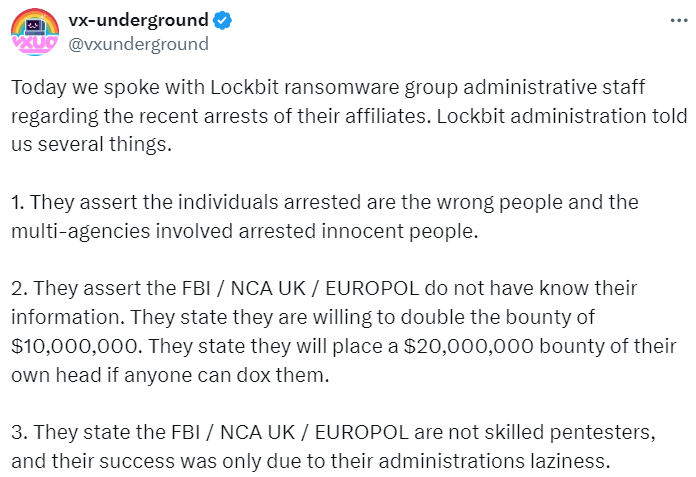
Lockbit ransomware group administrative staff make it clear that the group is not going anywhere. (Source – X).
Ukraine’s police service did not reveal the identities of the arrested father-son duo but announced the seizure of over 200 cryptocurrency accounts and 34 servers used by the gang in various countries, including the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States, and Britain.
The recent takedown of LockBit has been notable not only for its effectiveness but also for law enforcement’s unconventional methods, such as public trolling of the gang. However, experts warn that key members of LockBit might still be out of reach for Western law enforcement and could potentially resume operations or join other cybercrime groups.
Rafe Pilling, who leads Secureworks’ threat research unit, emphasizes that while arrests have been made, much of the disruption has been technical. He notes that LockBit’s significant damage was often inflicted by ‘affiliates’ — smaller hacking groups responsible for the initial break-ins. These hackers are still active and pose an ongoing threat.
Key arrests in Ukraine: targeting LockBit’s network
On February 21st, Ukrainian police announced the arrest of a father and son linked to the LockBit cybercrime gang.
The father and son were apprehended for their involvement in ransomware attacks targeting various institutions in France. During searches in Ternopil, a city in western Ukraine, law enforcement seized mobile phones and computer equipment used in these illegal activities.
The US has charged two Russian nationals in connection with deploying LockBit’s ransomware, and arrests have been made in Poland and Ukraine.
The Ukrainian police’s recent statement highlighted the seizure of over 200 cryptocurrency accounts and 34 servers in various countries, significantly impacting LockBit’s main hacking platform and other critical criminal infrastructure.
Before it was seized by police, LockBit could simultaneously extort multiple hacking victims through its website. This site listed the names of breached companies and organizations alongside a countdown timer that would trigger the release of a victim’s data unless a ransom was paid.
Monitoring LockBit’s evolution
Sophos X-Ops has been closely monitoring LockBit’s trajectory for over four years. The Sophos X-Ops incident response team’s analysis places LockBit among the top ten most frequently reported ransomware groups since 2020. With the decline of Conti in early 2022, LockBit surged in prominence, accounting for one-fifth of all ransomware infections seen by Sophos’s incident response team in 2023, mirroring Conti’s peak prevalence.
Chester Wisniewski, director and field CTO at Sophos, acknowledges the significant impact of the UK’s National Crime Agency (NCA) and its international partners in dealing a substantial blow to this dominant criminal ransomware syndicate. He notes that this operation has provided the most comprehensive insights into these groups’ operations since Conti’s fall in May 2022. The decentralized nature of these syndicates makes them particularly elusive.
Wisniewski points out key revelations about LockBit, noting that law enforcement appears to have gained access to the encryption keys used by LockBit, which could aid in the recovery process for victims. He also highlights the unfortunate truth that the criminals did not delete data, even for those who paid the ransom.
Despite a significant portion of LockBit’s infrastructure remaining online, Wisniewski does not expect a strong comeback for the group. He notes that such groups often rebrand and regroup under new names, continuing their malicious activities and evading sanctions.
Wisniewski cautions that the battle against LockBit may not be over. Members of the group who evade capture are likely to continue their cybercrime activities under different guises, as yet unwatched by law enforcement. He emphasizes the importance of continued vigilance against these evolving cyberthreats.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland


