
Scattered Spider is responsible for the cyberattacks in two Las Vegas casinos. (Image – Shutterstock)
Scattered Spider: 2023’s most powerful threat actor?
- Scattered Spider is apparently responsible for the cybersecurity incidents in two Las Vegas casinos
- The group uses social engineering attacks to gain credentials from victims.
- The group is now believed to have evolved to launch ransomware attacks on organizations as well.
The Scattered Spider hacking group has created a name for itself following the high-profile hacks in two Las Vegas casinos recently. While the group has been around for about a year plus, cybersecurity groups have acknowledged that Scattered Spider has evolved to do a lot more damage at this point in time.
In fact, according to a report by Mandiant Intelligence, Scattered Spider (codenamed UNC3944), is a financially motivated threat cluster that has persistently used phone-based social engineering and smishing (SMS phishing) campaigns to obtain credentials of its victims and launch cyberattacks.
Operating in underground communities and using Telegram, which continues to be the go-to social media app for cybercriminals, Scattered Spider activities have been reported since 2022. The Mandiant Intelligence report also shows that the group initially started enabling SIM-swapping attacks to support secondary criminal operations.
“However, in mid-2023, UNC3944 began to shift to deploying ransomware in victim environments, signaling an expansion in the group’s monetization strategies. These changes in its end goals signal that the industries targeted by UNC3944 will continue to expand,” the report revealed.
The cybersecurity company also directly observed the targets broaden in recent times. The group now targets the hospitality, retail, media and entertainment industries and well as financial services.
How Scattered Spider hacked MGM.
Scattered Spider’s modus operandi
The hacker group is known for its consistency and creativity. As such, it has managed to be increasingly effective in targeting cloud resources. Mandiant Intelligence pointed out that this strategy allows the threat actors to not only establish a foothold for future operations, but also perform network and directory reconnaissance while having access to many sensitive systems and data stores.
Unsurprisingly, they’re able to do it with minimal interaction as some organizations assume this activity is being performed by their own internal corporate network. With access to cloud environments, the group has persistence techniques that can be difficult to monitor and detect.
At the same time, the threat actors have used victims’ cloud resources to host malicious utilities and run them across systems in the network. In one incident, Mandiant explained that the threat actors hosted malicious utilities on an AWS S3 bucket, which was owned by the organization, and used an Intune PowerShell orchestration to download the utilities from inside the victim environment. Mandiant also observed the threat actor moving laterally within an organization’s Azure environment using the Special Administration Console to connect to virtual machines via serial console.
Meanwhile, another cybersecurity vendor, Trellix, believes that Scattered Spider uses POORTRY and STONESTOP to terminate security software and evade detection. POORTRY is a malicious driver used to terminate selected processes on Windows systems, like endpoint detection and response agents on an endpoint. To evade detection, attackers have signed the POORTRY driver with a Microsoft Windows hardware compatibility authenticode signature.
STONESTOP is a Windows userland utility that attempts to terminate processes by creating and loading a malicious driver. It functions as both a loader/installer for POORTRY, and an orchestrator to instruct the driver on what actions to perform.
In April 2023, the ALPHV (BlackCat) ransomware group used an updated version of POORTRY to compromise the U.S. payments giant NCR, leading to an outage on its Aloha point of sale platform.

Scattered Spider is becoming successful in its attacks.
It’s all connected: Scattered Spider, Roasted 0ktapus and Muddled Libra
Reports indicate that the group attacked around 130 organizations in 2022. In August 2022, cybersecurity company Group-IB Threat Intelligence published a report highlighting the group. Scattered Spider, then using the name of Roasted 0ktapus, targeted users of Signal. Twillio and Cloudflare also reported similar attacks during the same period last year.
According to Group-IB, the cybercriminals sent text messages containing links to phishing sites that mimicked the Okta authentication page of the organization to employees. The authentic-looking phishing site convinced users to enter their credentials, which Roasted 0ktapus then exploited. Group-IB also said the hackers were continuously monitoring their tools and using credentials as soon as they received them.
Months later, in December 2022, another cybersecurity vendor, CrowdStrike, also reported a campaign by Scattered Spider. The targets this time were the telecom and business process outsourcing sectors. Just as in the previous attacks, the aim was focused on gaining credentials to access the networks.
In June 2023, Palo Alto Networks’ Unit 42 investigated more than half a dozen interrelated incidents from mid-2022 through early 2023, which they attributed to the threat group Muddled Libra. Muddled Libra is believed to be a subset of Scattered Spider.
Muddled Libra’s tactics can be fluid – the cybercriminals can change account credentials within minutes of gaining access to a victim. Unit 42 also believes the group is focused primarily on the US, and its members speak English as a first language.
A report by Bloomberg stated that members of Scattered Spider are based in the US and UK, with some members believed to be as young as 19 years old. Citing cybersecurity researchers familiar with the group, the report also mentioned that one of the group members had a mid-Atlantic accent.
“Since our recent research publication, Muddled Libra has been associated with the BlackCat (aka ALPHV) ransomware group and we believe they are an affiliate. BlackCat is considered one of the most active and persistent ransomware groups in the last 12 months. We have seen at least 316 incidents posted on the BlackCat leak sites in the previous 12 months. BlackCat gives affiliates access to their kit, which includes the compiled ransomware binaries, support, negotiations and access to their leak site,” stated the Unit 42 report.
Unit 42 also highlighted that the threat group has repeatedly demonstrated a strong understanding of the modern incident response framework. This knowledge allows them to continue progressing toward their goals even as incident responders attempt to expel them from an environment. Once established, this threat group is difficult to eradicate, a situation that MGM is currently facing with Scattered Spider.
“Muddled Libra has shown a penchant for targeting a victim’s downstream customers using stolen data and, if allowed, they will return repeatedly to the well to refresh their stolen dataset. Using this stolen data, the threat actor has the ability to return to prior victims even after the initial incident response. This demonstrates the attacker’s tenacity even after initially being discovered,” Unit 42 added.
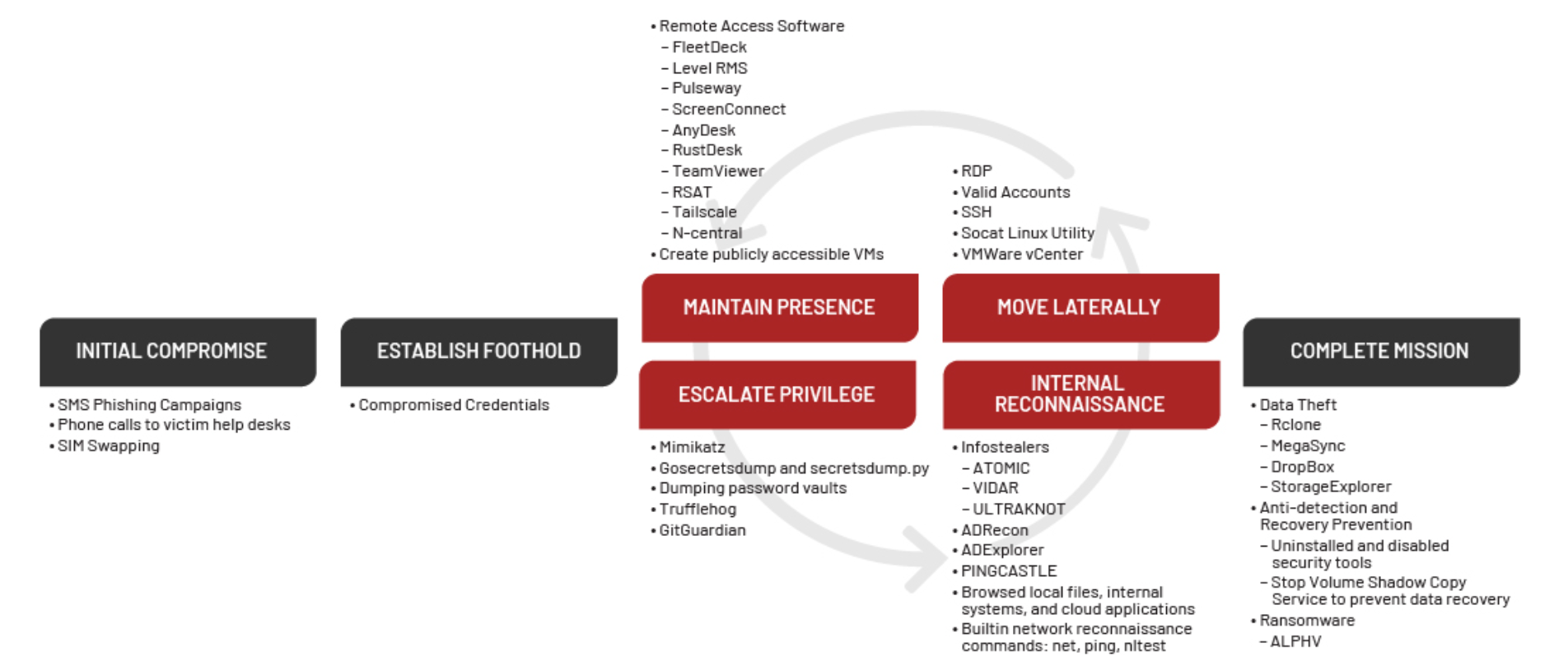
UNC3944 attack lifecycle. (Source – Mandiant)
Social engineering attacks
All the cybersecurity vendors investigating the threat actor have acknowledged that Scattered Spider is a very tricky threat. While there are means to protect businesses and mitigate these threats, social engineering attacks remain a constant problem for organizations all over the world.
In fact, statistics have indicated that social engineering attacks continue to be a big problem for organizations in the U.S. As of 2022, 46% of organizations in the U.S. and 93% of individuals have been a victim of social engineering. However, social engineering has only been addressed by 27% of American organizations. These organizations claim to have security awareness training programs on social engineering. But is it enough?
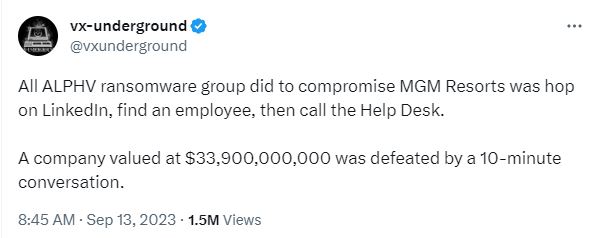
There have been Tweets stating that all Scattered Spider had to do to get access to MGM was to get onto LinkedIn, find an employee and call the helpdesk to get credentials. While this statement has yet to be proven, it clearly shows a lack of seriousness in cybersecurity if it is true.
Cybercriminals are aware that employees are the weakest link in an organization’s cybersecurity posture. And social engineering attacks are proving to be the easiest way to infiltrate organizations today. Be it social media, SMS, emails or even calling helpdesks, all it takes is for one employee’s credentials to be compromised for cybercriminals to launch a full-scale cyberattack.
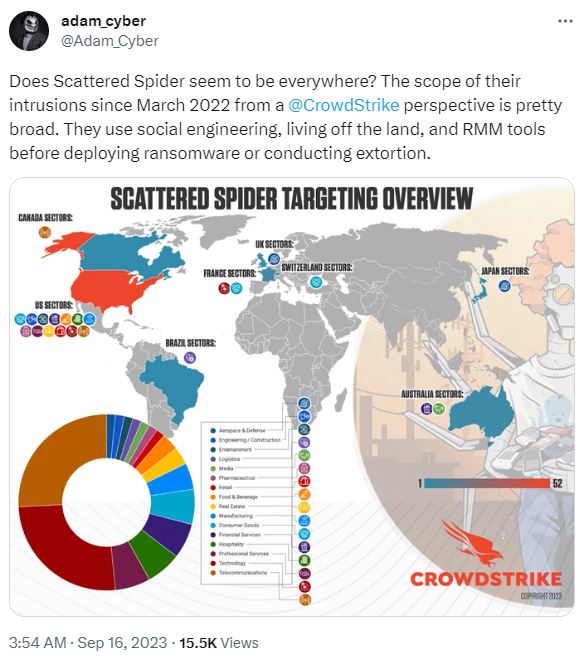
The scope of Scattered Spider’s attack network.
Scattered Spider shows no sign of slowing down
Mandiant Intelligence also believes that Scattered Spider will continue to evolve and broaden its skills and tactics to target more victims in the future.
“We expect these threat actors will continue to improve their tradecraft over time and may leverage underground communities for support to increase the efficiency of their operations. The threat actors have successfully relied on social engineering schemes to obtain initial accesses, whether in the form of SMS phishing campaigns or by calling victim organizations’ helpdesks to reset passwords and multi-factor authentication,” stated Mandiant.
The success the group is having is likely to be a catalyst in expanding its reach to more disruptive and profitable attacks. In the recent cybersecurity incidents involving the two casinos in Las Vegas, Caesars Entertainment Inc. is believed to have paid the ransom to get access to its system while MGM is still investigating with the FBI.
“We anticipate that intrusions related to UNC3944 will continue to involve diverse tools, techniques and monetization tactics as the actors identify new partners and switch between different communities,” concluded Mandiant.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland






