
(Source – Shutterstock)
Apple boosts security with lockdown mode for mobile devices
In 2021, Apple found itself dealing with spyware problems after reports of mobile devices being easily hacked. The Pegasus spyware by NSO Group was reported to be able to take control of Apple devices remotely, turning them into spying tools.
The spyware was exposed by investigative reports last year and showed several governments using the tool to spy and monitor the conversations of selected individuals. Among the countries involved included India, which saw huge protests calling out those responsible for using the spyware to spy on politicians and prominent individuals.
Developed and licensed by NSO Group, the Pegasus spyware can infect billions of mobile devices, be it on iOS or Android operating systems. Once a mobile device is affected by the spyware, victims could have their messages, calls, and photos copied as well as have their mobile phones turned into listening and tracking devices. Since the exposure, Apple has announced several updates and patches to deal with the spyware.
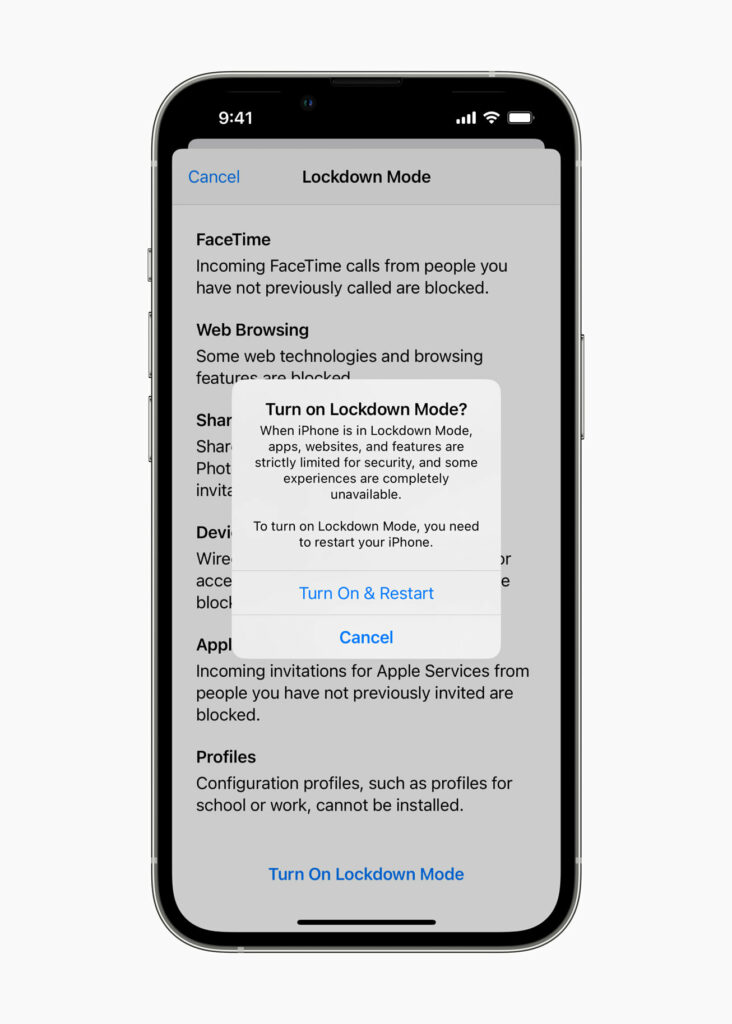
Now, Apple has detailed initiatives it hopes can protect users who may be targeted by spyware. This includes Lockdown Mode, extreme, optional protection for the very small number of users who face grave, targeted threats to their digital security. This included the Pegasus spyware as well as other mercenary spyware being devolved.
(Source – Apple)
At launch, Lockdown Mode includes the following protections:
- Messages: Most message attachment types other than images are blocked. Some features, like link previews, are disabled.
- Web browsing: Certain complex web technologies, like just-in-time (JIT) JavaScript compilation, are disabled unless the user excludes a trusted site from Lockdown Mode.
- Apple services: Incoming invitations and service requests, including FaceTime calls, are blocked if the user has not previously sent the initiator a call or request.
- Wired connections with a computer or accessory are blocked when iPhone is locked.
- Configuration profiles cannot be installed, and the device cannot enroll into mobile device management (MDM), while Lockdown Mode is turned on.
According to Ivan Krstic, Apple’s head of Security Engineering and Architecture, Lockdown Mode is a groundbreaking capability that reflects the company’s unwavering commitment to protecting users from even the rarest, most sophisticated attacks.
“While the vast majority of users will never be the victims of highly targeted cyberattacks, we will work tirelessly to protect the small number of users who are. That includes continuing to design defenses specifically for these users, as well as supporting researchers and organizations around the world doing critically important work in exposing mercenary companies that create these digital attacks,” commented Krstic.
Over time, Apple is expected to continue to strengthen Lockdown Mode and add new protections. To invite feedback and collaboration from the security research community, Apple has also established a new category within the Apple Security Bounty program to reward researchers who find Lockdown Mode bypasses and help improve its protections.
Bounties are doubled for qualifying findings in Lockdown Mode, up to a maximum of US$2,000,000 — the highest maximum bounty payout in the industry.
At the same time, Apple is also making a US$10 million grant, in addition to any damages awarded from the lawsuit filed against NSO Group, to support organizations that investigate, expose, and prevent highly targeted cyberattacks, including those created by private companies developing state-sponsored mercenary spyware.
Spyware not only targeting Apple
Meanwhile, Google last month said that an Italy-based firm’s hacking tools were used to spy on Apple and Android smartphones in Italy and Kazakhstan, casting a light on a “flourishing” spyware industry. Google’s threat analysis team said spyware made by RCS Lab targeted the phones using a combination of tactics including unusual “drive-by downloads” that happen without victims being aware.
Google said it warned Android users targeted by the spyware and ramped up software defenses. The Google threat team is tracking more than 30 companies that sell surveillance capabilities to governments, according to the Alphabet-owned tech titan.
“The commercial spyware industry is thriving and growing at a significant rate,” Google said.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


